
Secure Credit Union Website Hosting That Just Works
Credit unions and other financial institutions are facing growing pressure



Imagine your business network as a high-security office building. You’ve installed surveillance cameras (firewalls), built a reinforced vault for sensitive data (backups), and stationed a security team to monitor activity (IT staff). But here’s the catch: every laptop, desktop, server, and IoT gadget connected to your network represents a potential entry point, like dozens of front doors scattered throughout your building, each open to possible vulnerabilities.
Cybercriminals understand these front doors as ways to enter a business. Without robust endpoint security solutions protecting these access points, you’re leaving your digital doors wide open for attackers to walk right in.
Your endpoints — laptops, desktops, and servers — are the bridge between your team and your business systems. They’re where work gets done and where most cyberattacks begin. Every email opened, link clicked, file downloaded, and website visited creates an opportunity for malicious actors to strike.

In 2025, the risks are higher than ever:
Soaring breach costs: The average U.S. data breach now costs a record-breaking $10.22 million, up 9% from last year (IBM).
Operational paralysis: A Denial of Service (DoS) attack overwhelms and cripples systems, stopping operations until the attacker’s demands are met. It’s one of the most common breach patterns, which can result in expensive downtime and more potential financial loss (Verizon DBIR 2025).
Targeting SMBs: Small to mid-sized businesses are being targeted nearly 4x more than large enterprises (Verizon DBIR 2025).
Ransomware on the rise: Ransomware was present in 44% of all breaches analyzed, an increase from the previous year, which was 32%. This increase shows the importance of having a strong, multi-layered cybersecurity stack (Verizon DBIR 2025).
Follow the money: 87% of breaches were driven by financially motivated external actors (Verizon DBIR 2025).
That’s why Endpoint Detection & Response (EDR) has become a critical layer of modern cybersecurity. While perimeter defenses like firewalls and antivirus remain essential, they can’t always spot or stop every threat. EDR helps close that gap, continuously monitoring devices, detecting suspicious behavior in real time, and stopping attacks before they can cause real damage.
Traditional antivirus is like a basic security guard checking IDs, it matches files against a list of known threats. That’s fine for some attacks, but not all of Today’s cyberattack tactics, such as:
Zero-day exploits: exploiting unknown vulnerabilities (Security Scorecard)
Fileless malware: operating in memory without leaving a signature, making it harder to detect (Crowdstrike 1).
Living-off-the-land attacks: fileless malware cyberattack abusing legitimate system tools (CrowdStrike 2).
Polymorphic malware: constantly changing its code to avoid detection (SentinelOne).
Today, EDR can be one of the most critical layers of security because of its ability to monitor, alert, and stop malicious activity 24/7/365.

EDR is like an elite security team with advanced surveillance and instant response capabilities:
With perimeter security as your first line of defense and EDR as a critical second line, your endpoints can go from being potential weak spots to fortified assets.
A remote employee opens a phishing email on his laptop with a malicious attachment. Having no idea, he clicks the attachment. Traditional antivirus might have missed it, but EDR notices the file trying to encrypt documents at 2 AM, cuts the endpoint (the employee’s laptop) off from the network, and alerts the team of engineers and your security team, potentially halting the ransomware attack in its tracks. This saves you time, money, and a lot of stress.
Cyber threats are evolving at a pace we’ve never seen before, and your endpoints are often the first line of defense. As attackers adopt new tools and tactics, simply relying on traditional protection isn’t enough. Recent industry reports from IBM, Verizon, and NMFTA reveal several disturbing trends that are reshaping the cybersecurity landscape.
The takeaway? Cyberattacks are evolving, and your cybersecurity stack needs to go beyond the basics. Modern endpoint protection, paired with strong monitoring, threat hunting, and rapid response capabilities, can help you detect, contain, and stop these threats before they cause costly downtime or data loss.
When it comes to cybersecurity investments, you can’t just ask, “Is it secure?”, you also need to ask, “Is it worth it?” For many businesses, endpoint security — especially tools like Managed Endpoint Detection & Response (EDR) — delivers both peace of mind and a powerful return on investment.
Strong endpoint security solutions deliver:
When it comes to Managed Endpoint Detection & Response (EDR), automation alone isn’t enough. That’s why DataYard has partnered with Huntress, a leader in human-powered threat detection, to deliver a security solution that goes beyond alerts; it stops threats at the source and delivers answers.
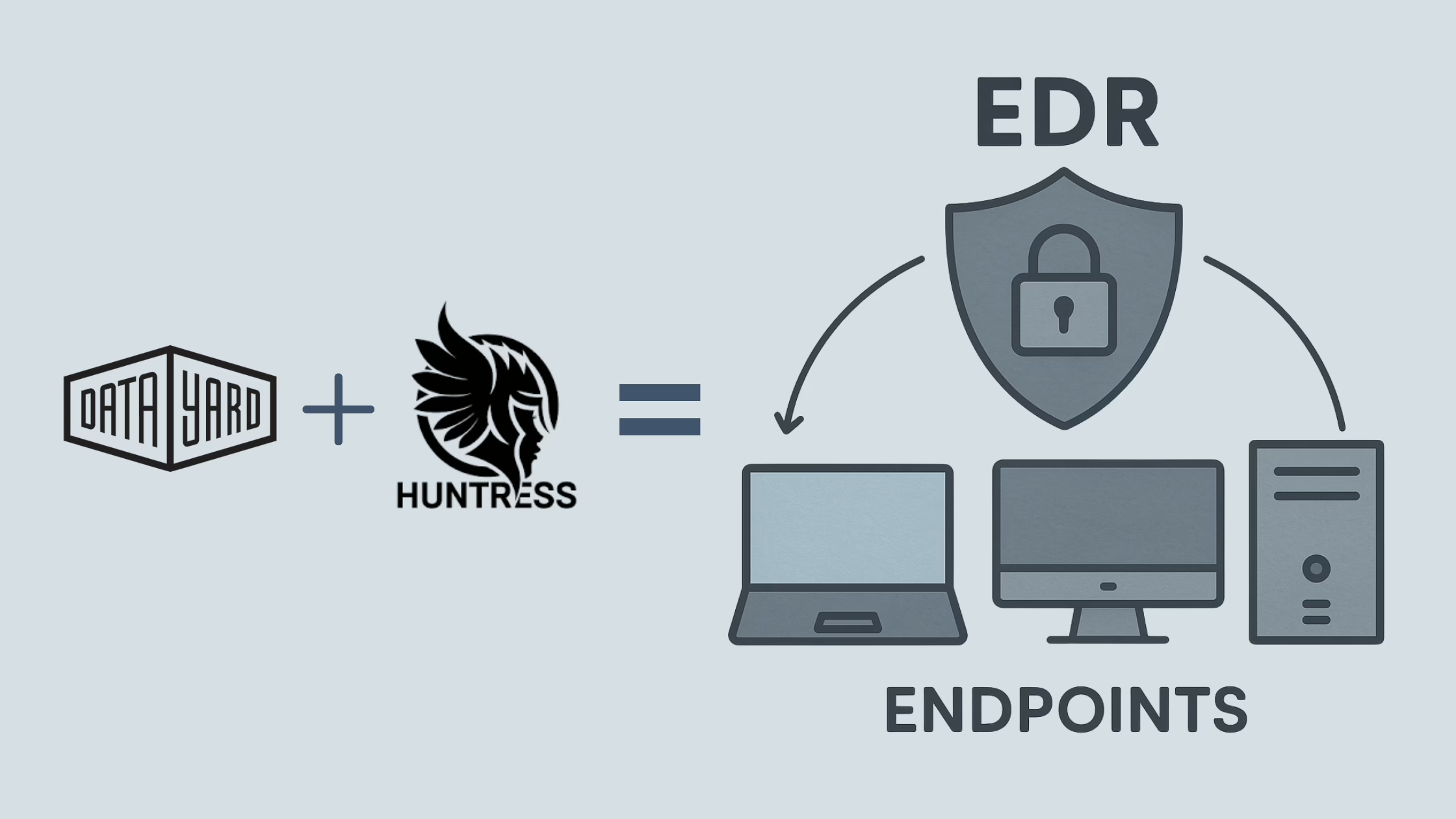
While many EDR tools stop at automated detection, our Huntress-powered EDR platform combines cutting-edge technology with a 24/7 Security Operations Center (SOC) that actively investigates suspicious activity.
The result? Instead of just telling you there’s a problem, you get rapid remediation with expert analysis 24/7/365.
With Huntress in our corner, DataYard’s endpoint security solutions don’t just detect and block threats; they actively hunt them down and walk you through remediation. You gain faster response times, fewer false alarms, and the confidence that both machine intelligence and human expertise are monitoring your business 24/7.
If 2025 is the year you want to stop wondering whether your business could survive a cyber incident, the Huntress + DataYard’s Managed EDR solution is your answer.
As a DataYard client, this partnership gives you:
This isn’t just about stopping ransomware. It’s about helping to prevent threats from gaining a foothold.
Paired with an EDR solution like DataYard’s, these proven security processes can help give your business the strongest possible defense:
Join our free 45-minute cloud cybersecurity webinar on:
In this online webinar you’ll learn
Every attendee receives:
Sit down with a DataYard cybersecurity specialist to evaluate your endpoint security strategy, so you can close gaps, reduce risk, and keep your business safe from evolving threats.
Q: How are endpoint and network security different?
A: Network security protects data in transit between systems, while endpoint security protects the devices where your users work (laptops, desktops, servers, mobile devices). Both are essential. If you’re unsure what you need, contact us with your security questions.
Q: Is EDR affordable for small to mid-size businesses?
A: Yes, managed EDR scales to any size organization and avoids large upfront investments. Many businesses use EDR as a service to get enterprise-grade protection at a predictable monthly cost.
Q: Will it slow my devices down?
A: Modern EDR solutions are designed to run efficiently in the background with minimal performance impact, even during active threat monitoring.
Q: How fast does it detect new threats?
A: Most advanced EDR platforms detect suspicious activity within seconds and can automatically contain threats likely before they spread, which is critical for fast-moving attacks like ransomware.
Q: What if a breach still happens?
A: EDR’s forensic tools provide detailed insight into how the attack occurred, what systems were affected, and the best remediation steps, helping you to recover faster and prevent repeat incidents.
Q: Does EDR replace antivirus software?
A: Not exactly. EDR is more advanced and includes continuous monitoring, automated response, and threat hunting, but many organizations run Endpoint Detection & Response (EDR) alongside modern antivirus for layered protection. Not sure what’s right for your cybersecurity stack? Let’s talk, we offer free consultations.
Your business deserves comprehensive protection, not checkbox security approaches. You need experienced partners who prioritize uptime, data protection, and ransomware resilience as seriously as you do.
DataYard provides that partnership.
Contact us to get a free consultation.
Email: [email protected]
Phone: 937-226-6896 option 2
Learn More: Security Services
Schedule Your Free RISE IT RISK Assessment: Get Your Assessment
References
CrowdStrike 1- Fileless Malware Explained
https://www.crowdstrike.com/en-us/cybersecurity-101/malware/fileless-malware/
CrowdStrike 2 – What Are Living off the Land (LOTL) Attacks?
https://www.crowdstrike.com/en-us/cybersecurity-101/cyberattacks/living-off-the-land-attack/
IBM Security – Cost of a Data Breach Report 2025.
https://www.ibm.com/reports/data-breach
NMFTA – Ransomware as a Service: What You Need to Know to Protect Against a Growing Threat
https://nmfta.org/ransomware-as-a-service-what-you-need-to-know-to-protect-against-a-growing-threat/
Security Scorecard – What Is a Zero-Day Exploit and Why Is It So Dangerous?
https://securityscorecard.com/blog/what-is-a-zero-day-exploit-and-why-is-it-so-dangerous/
SentinelOne – What is Polymorphic Malware? Examples & Challenges
https://www.sentinelone.com/cybersecurity-101/threat-intelligence/what-is-polymorphic-malware/
Silent Breach – The true cost of a cybersecurity attack
https://silentbreach.com/BlogArticles/the-true-cost-of-a-cybersecurity-attack/
Verizon – 2025 Data Breach Investigations Report. https://www.verizon.com/business/resources/reports/dbir/
Disclaimer:
This content is provided for informational purposes only and should not be considered legal, compliance, or security advice. Cybersecurity threats evolve rapidly, and no solution, including those mentioned, can guarantee complete prevention of every possible attack. For guidance tailored to your organization’s specific needs, please consult directly with our qualified cybersecurity professionals.

Credit unions and other financial institutions are facing growing pressure
Cloud cost optimization in 2026 isn’t just about cutting spend

Phishing remains one of the most dangerous cyber threats facing