
Secure Credit Union Website Hosting That Just Works
Credit unions and other financial institutions are facing growing pressure

Security teams and company executives typically agree on one thing when it comes to cybersecurity: “We are constantly under attack.” It’s easy to see when we look around and see news headlines from all around the world concerning data breaches, exploits, and ransomware. With the public perception surrounding these announcements, it can start to worry decision makers and IT professionals. What’s worse is turning those abstract worries into concrete decisions about where to invest time, people, and funding. Approaching security operations from only a reactive or defensive perspective may not always grant you the insight needed into your organization’s unique risks at any given point in time.
Red and Purple Teaming engagements give organizations a realistic and repeatable way to discover real weaknesses, validate security controls, evaluate personnel response, and help build the confidence that you can contain an event or even avoid becoming a headline — before an actual adversary forces the issue.
Organizations routinely buy security controls, check compliance boxes, and assume protection will follow. This behavior creates two problems for leadership:
The Result: Leadership is left managing perception rather than measurable exposure.
The Solution: Red & Purple Teaming
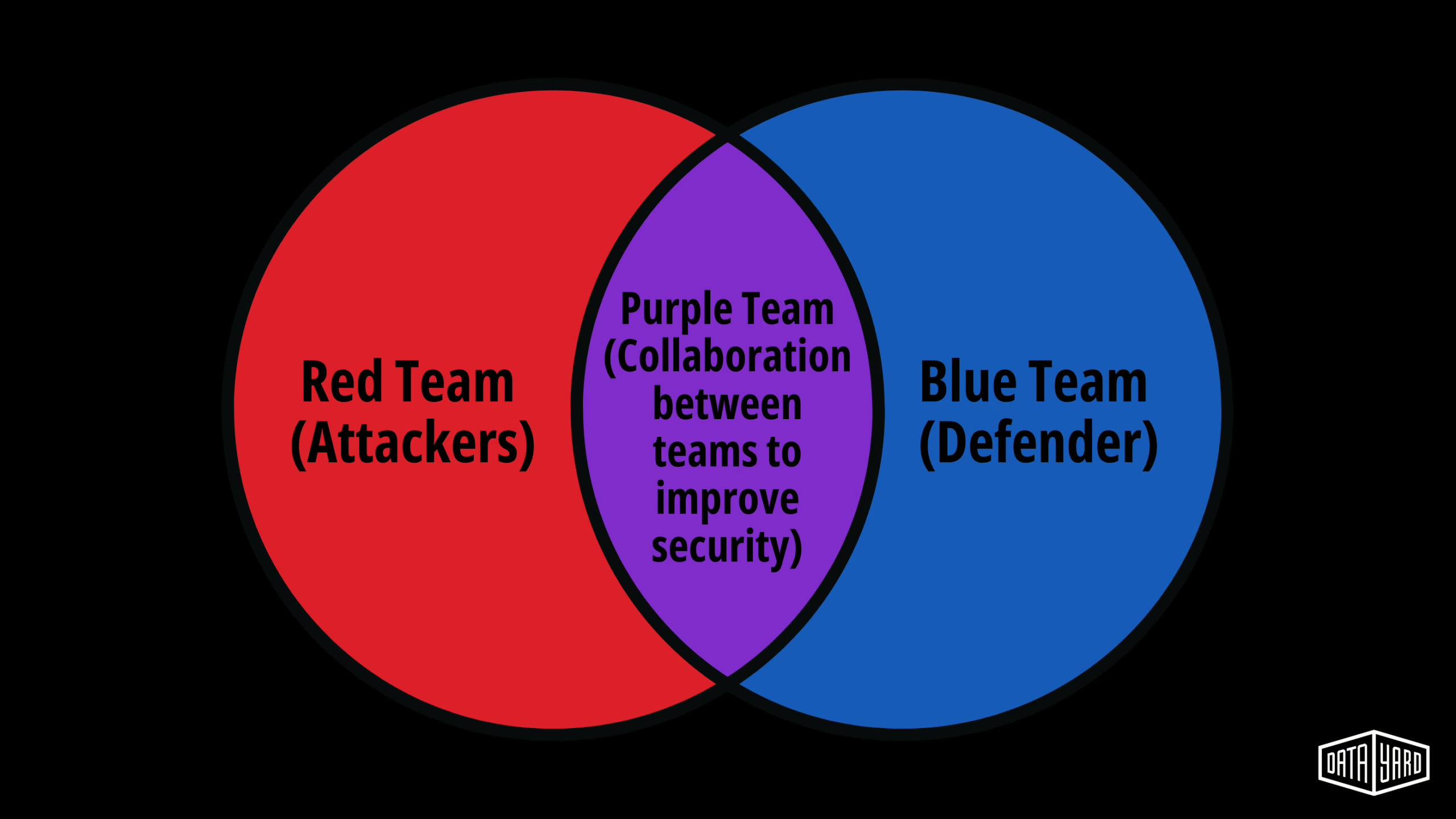
Red Teaming is adversary emulation, and Purple Teaming is a collaboration between Red and Blue (defender) teams. Using both concepts allows for structured ways to test real-world outcomes. Tangible benefits of these include:
You can either hope your security controls work, or you can actually validate whether or not they do.
• Risk reduction with evidence: For company boards and executives, their reporting is now evidence-based: “we tested X, found Y, and remediated Z” — instead of subjective assurances. Concrete findings and solutions are proof of forward progress.
• Better allocation of budget: Remediation guided by Red Team findings can target the most likely and highest-impact gaps. Once you understand that, you properly understand your risk profile (i.e. — knowing your enemy).
• Faster detection and response: Exercises can improve incident playbooks, detection tuning, and response times – with the added benefit of enlightening your team on how they can create more robust solutions from the start of each project, in order to avoid frantic incident response situations altogether.
• Culture of continuous improvement: Regular exercises bypass ego, normalize imperfect outcomes, and make learning iterative rather than punitive. If you’re looking for measurable progress, concrete findings and goals are much more beneficial than faith and subjective perspectives.
1. Start small and focused. Pick a high-risk business process or system and run a scoped attack simulation against it.
2. Define success metrics. Time-to-detect, time-to-contain, number of control failures, what business impacts were avoided, etc.
3. Make it collaborative. Run Purple Team sessions so Blue learns from Red in real time.
4. Prioritize fixes by risk and cost. Not all findings are equally urgent — fix the things that materially reduce risk first. And understand which risks are relevant to your organization.
5. Repeat and scale. Treat this as ongoing resilience testing, not a one-time audit.
When proposing a red team exercise to business owners or company executives, it’s not uncommon to hear some hard questions and objections come up. This is completely normal and expected. Especially when nothing of this sort has intentionally been done before. The fear of the unknown is a powerful motivator.
Here are some common objections and how to navigate through them:
“Nobody would want to breach us.”Many organizations believe they are too small or unattractive as a target. Unfortunately, attackers don’t see it that way. They target opportunities. Whether because your data is valuable, or because comprising your systems is simply a means to an end in an grander campaign, knowing what makes your organization susceptible to bad actors helps focus your defenses where they matter most.
“Our vendor controls should be enough.”We simply cannot operate our SOCs under an assumption-only model, trusting that the vendors’ solutions will keep us safe. These solutions are tools, and tools can be used improperly or bypassed entirely. Training against realistic threat behaviors teaches you how to use these tools effectively and determines where their real limits are.
“We can’t afford disruptions.”Scoped exercises and well thought out rules of engagement prevent business from being impacted while still uncovering the most critical gaps. The goal of offensive security drills is to emulate malicious activity safely. There are plenty of tools at a business’ disposal to run a safe security exercise.
“We can’t afford this in general.”While this could be true, a follow-up question would be: “Can you afford the aftermath of a security breach?”. This is when organizations should work to understand their risk profile and, based on those findings, make a decision on how to invest time and resources for protecting their business.
Organizations that treat cybersecurity as a static checkbox are putting themselves at a disadvantage. Red and Purple Teaming can transform your uncertainty into prioritized action, improve event detection and response, and assist organizational leaders in making smarter choices and investments in resilience. In short: if you want to protect your most valuable business assets, you should plan to know your adversary. There are many adversaries out there who seek any opportunity to take, disrupt, or exploit — and now is the time to prepare for their inevitable attempts.
You don’t need to wait for an incident to understand your exposure. Our security team can help you identify where gaps may exist today — and talk through whether adversary-style testing could be a smart next step for your organization. It starts with a conversation and a clear picture of your infrastructure.
Disclaimer:
The techniques described in this article, including Red and Purple Teaming, are performed only in controlled, authorized environments under clearly defined scopes and legal agreements. DataYard does not support or encourage unauthorized testing, scanning, or intrusion activities of any kind. Always consult with qualified professionals before undertaking any security assessments.
—
Author: Alex Messham — Information Security Professional, Red Teaming & Adversary Emulation, Operations Engineering.
Edited: Mike Beagles – Vice President of IT Operations, CySec Ops
Edited: Natalie Mezera – Director of Client Partnerships

Credit unions and other financial institutions are facing growing pressure
Cloud cost optimization in 2026 isn’t just about cutting spend

Phishing remains one of the most dangerous cyber threats facing